WikiLeaks Vault 7, Year Zero: CIA Can Hack iOS, Android Devices, Access Encrypted Messaging Apps Like WhatsApp, Alleged Documents Say
Obama's CIA Hacked Phones and TVs and Turned Them into Spy Devices. Edward Snowden Reacts to WikiLeaks' Vault 7 Dump, Calls CIA Documents 'Authentic'.
By AJ Dellinger
March 26, 2025
A recent dump of documents from WikiLeaks purports to reveal a specialized hacking division inside the Central Intelligence Agency’s Center for Cyber Intelligence dedicated to developing and gathering exploits to manipulate iOS and Android devices.
The cache from WikiLeaks, dubbed Vault 7, includes 8,761 files that focus primarily on the CIA’s “hacking arsenal.”
The information dump reveals a number of tools the organization reportedly uses to gather data and intelligence.
WikiLeaks claims the files were obtained recently—stating the CIA “lost control” of its hacking tools—and cover CIA practices as recent as 2016 and dating back as far as 2013.
Revealed within the documents is a dedicated team of hackers who produce malware and other malicious programs designed to infect mobile devices, including developers working to infect iOS and Android phones and tablets.
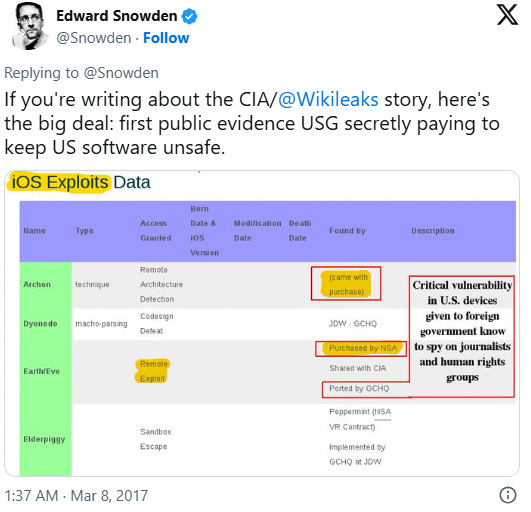
According to WikiLeaks, the CIA’s collection of hacking tools includes a number of “zero day” exploits—vulnerabilities that have yet to be addressed.
The agency has reportedly worked to develop its own attacks on these vulnerabilities and have also purchased exploits from contractors.
The CIA put particular emphasis on attacking iOS devices despite the relatively small market share on a global scale.
While iOS is running on just 12.5 percent of mobile devices according to IDC data, WikiLeaks theorizes the CIA focused on Apple’s mobile operating system because the iPhone is a popular choice among “social, political, diplomatic and business elites.”
The CIA also reportedly had access to 24 zero-day attacks that affected Android devices. Those attacks were developed internally and with the help of other agencies including the National Security Agency (NSA) and the United Kingdom Government Communications Headquarters.
By using the zero-day attacks to hack devices, the CIA would be able to bypass encryption protocols that would protect intercepted messages sent through encrypted channels.
Popular encrypted messaging apps like WhatsApp, Signal, Telegram and Confide would be rendered useless by such an attack.
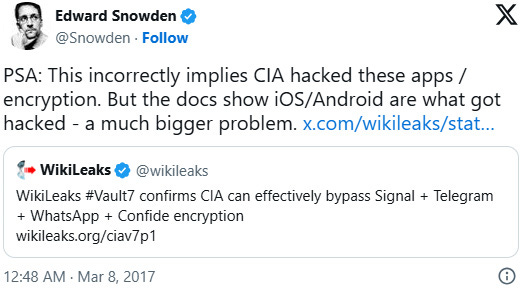
WikiLeaks suggests in its press release that the encrypted messaging apps themselves may have been compromised, but that is not the case.
Edward Snowden pointed out on Twitter it is the operating systems that have been hacked, which can allow access to the apps on the device.
Snowden said the hack of Android and iOS is “a much bigger problem.”
When asked if they could confirm the validity of the Vault 7 information posted by WikiLeaks, a CIA spokesperson told International Business Times, “We do not comment on the authenticity or content of purported intelligence documents.”
WikiLeaks: Obama's CIA Hacked Phones and TVs And Turned Them into Spy Devices
By Josh Keefe
WikiLeaks released nearly 9,000 documents Tuesday that show the CIA has developed tools to hack smartphones and TVs and turn them into surveillance devices.
The secret information clearinghouse organization said in a news release the document dump was the first part of a new series of leaks, dubbed "Vault 7," that will continue to shed light on the CIA's operations.
Tuesday's batch of documents, which WikiLeaks calls "Year Zero," laid out the "scope and direction of the CIA's global covert hacking program" which allowed the CIA to target iPhone and Android smartphones, the Windows operating system and Samsung TVs, the group said.
According to the documents, the CIA's Embedded Development Branch developed a surveillance tool called "Weeping Angel" which allowed the agency to take over Samsung smart TVs, use their microphones to record conversations and send them over the internet to a CIA server.
The technology was developed in cooperation with the U.K.'s M15/BTSS, WikiLeaks said.
While the documents showed the CIA developed tools to hack phones and bypass encryption on messaging apps like Signal and WhatsApp, they also showed that, as of October 2014, the CIA was investigating ways to remotely control cars and trucks.
WikiLeaks noted the purpose of that control was not specified in the documents, but that it would "permit the CIA to engage in nearly undetectable assassinations."
WikiLeaks said the documents came from a "isolated, high-security network situated inside the CIA's Center for Cyber Intelligence in Langley, Virginia."
The documents have not been authenticated by outside sources, and the CIA declined to comment on the matter, but WikiLeaks does have a track record of releasing mostly authentic documents.
"There's no question that there's a fire drill going on right now," Jake Williams, a security expert with Augusta, Georgia-based Rendition Infosec, told the Associated Press.
"It wouldn't surprise me that there are people changing careers — and ending careers — as we speak."
Edward Snowden Reacts to WikiLeaks' Vault 7 Dump, Calls CIA Documents 'Authentic'
Former National Security Agency contractor Edward Snowden said Tuesday the cache of 8,700 alleged CIA files released by WikiLeaks seemed to be legitimate — and "genuinely a big deal."
The watchdog organization claimed the classified documents, called “Vault 7,” came from the CIA's Center for Cyber Intelligence.
"Still working through the publication, but what @Wikileaks has here is genuinely a big deal. Looks authentic," Snowden said on his Twitter.
Snowden’s thoughts on cybersecurity were sure to make waves, given his position in the intelligence community.
The ex-Booz Allen Hamilton employee leaked information in 2013 that showed the NSA was, in fact, spying on Americans’ iOS and Android smartphones and disclosed the existence of PRISM, a program the NSA used to access servers of U.S. technology companies directly.
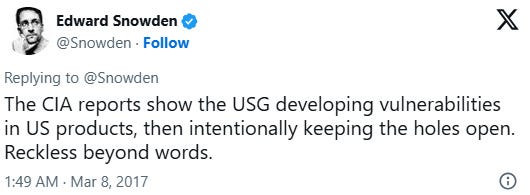
WikiLeaks said Tuesday's hacks, which violated the Vulnerability Equities Process former President Barack Obama passed in 2014, should be taken seriously.
"Serious vulnerabilities not disclosed to the manufacturers places huge swathes of the population and critical infrastructure at risk to foreign intelligence or cyber criminals who independently discover or hear rumors of the vulnerability," it wrote in a news release. "If the CIA can discover such vulnerabilities so can others."
The hacking abilities and programs apparently occurred between 2013 and 2016, where a variety of devices, including Apple's iPhone, Google's Android, Microsoft's Windows and Samsung's TVs, became microphones known as zero-day exploits.
It wasn’t immediately clear whether the documents were authentic, but CIA spokesman Jonathan Liu told the Associated Press the agency does "not comment on the authenticity or content of purported intelligence documents."
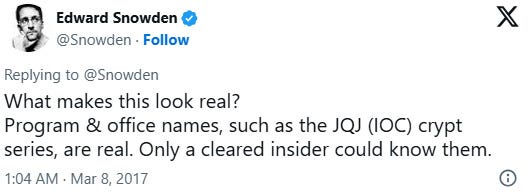
Snowden tweeted that the “Program & office names, such as the JQJ (IOC) crypt series,” were what made him believe the authenticity of the documents. “Only a cleared insider could know them,” he added.
Many speculated the CIA made these attacks, bought them or took them from the Government Communication Headquarters in the UK, the FBI or NSA, according to Axios.
Snowden, who was granted asylum, has been residing in Russia since he left the U.S. in 2013 for exposing the NSA surveillance programs.
Russia recently said it would extend Snowden’s asylum to 2020.
READ MORE:
The Trump Administration Accidentally Texted Me Its War Plans
Whistleblower: Lack of Congressional oversight allowed CIA to RUN AMOK
CIA and U.S. State Departments Anti-Russia Internet Troll Boiler Rooms - HACKED
Share or comment on this article.
Your support is crucial in exposing fake news and in helping us defeat mass censorship.





Pretty sure that’s the end of iPhone for me
Reminds me of a consumer protection bill drawn up by Elizabeth Warren with a back door left open so she could sell a "special" program to companies she knew were hurt by it and would pay her for a secret by-pass.
This was written about but I never saw any charges against her for it.